Cyber Security
Solutions
At PBG Networks, our security methodology follows the CSF to identify and quickly recover from current and future security vectors. Ready to learn more? Call PBG today.

Virtual Image vs. Hardened Virtual Image
Virtual images reside on the cloud and let you cost-effectively perform routine computing operations without investing in local hardware and software.
Hardening is a process of limiting potential weaknesses that make systems vulnerable to cyber-attacks.

Is Your VPN too Trusting?
The Pandemic has intensified the need for remote access. VPNs might seem like the quick solution, but a VPN by itself leaves your network vulnerable to malware and ransomware. Incorporating micro-segmentation will limit user access to the network with no change in user experience. Learn more about how PBG can help you implement micro-segmentation on your network.
Managed Security Services (MSS)
Let PBG Networks take the burden off of your Organization by providing assistant services necessary to operate and manage your security investment.

Ransomware: How to Limit Your Risk
Ransomware is becoming a major risk to organizations. Adding scare tactics and intimidation to malware has cost many organizations huge amounts of time and money. Prevention is key.
Make Your Cyber Security Future Brighter
The Risks
In an ever evolving world, Cyber Security is always moving forward and changing. As a result, organizations are forced to be more and more proactive to remain safe and keep up to date. Any plan implemented needs to be all inclusive and adaptable to combat today’s ever increasing numbers of cyber criminals, viruses, and ransomware attacks and protect their most sensitive data.
Success Comes with a Plan
The Solution
Having a strong Cyber Security Strategy mitigates risk. Today’s best practices ensure a quick recovery from current and future security vectors.
Our security methodology follows the CSF governance model. This model helps to evaluate your current security practices, establish and improve upon your present security posture, and aid decision makers in the buying process. CSF is not meant to replace your cybersecurity operations, but rather is a complement to your existing business.

Covering All the Bases
At PBG Networks we encourage a well rounded and multi-factor approach

Hardened Virtual Image

Managed Security Services

MFA and Zero Trust
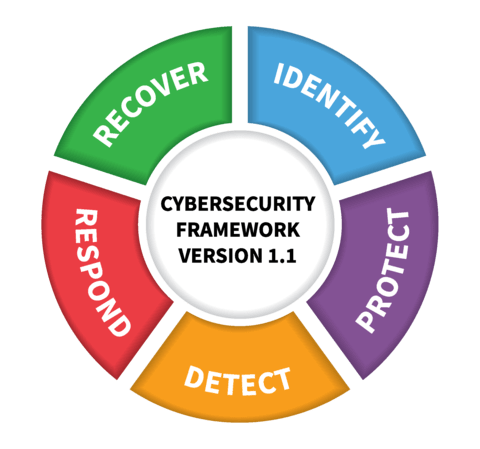
Our Security Methodology Follows the CSF to Identify and Quickly Recover Security Vectors
-
Identify:
Solutions that identify and inventory assets and vulnerabilities that reside on devices, applications, and networks. They will help you gain an institutional understanding of what systems need to be protected and help to identify your current attack surface.
-
Protect:
Prevent or limit the impact of cyber-attacks through access control, data security, patch management and maintenance, and protective methods. These solutions help you protect various asset classes like workstations, network devices, software applications, networks, data, and users.
-
Detect:
These solutions will allow you to detect cybersecurity events and anomalies that occur within devices, applications, and networks. They can assess the potential impact of an event by, discovering anomalous activity, continuously monitor information assets, hunt for intrusions, and provide security analytics.
-
Respond:
Take action and respond once a cybersecurity event is detected. These solutions assist by eradicating intrusion footholds and assessing the damage caused by an attack.
-
Recover:
These solutions help you return to normal operations after an undesirable cybersecurity event by restoring capabilities, services that were impaired and documenting lessons learned.